You know what would be or what would realizar un MitM (Man in the Middle) con Ettercap?
MitM is a attack is that we introduce in the middle of an exchange of data between two computers is giving or systems. The intention is that as traffic passes through us, we can intercept the packets and decrypt data of interest.
This is used for cybercriminals, Destructively, but also it is a procedure carried out audits to check how the network security or software.
Knowing that this often happens, it is logical to think the importance of data security for businessesFor example, because nobody wants to have spies who know what to send and, worst of all, they work to get information that can make us vulnerable.
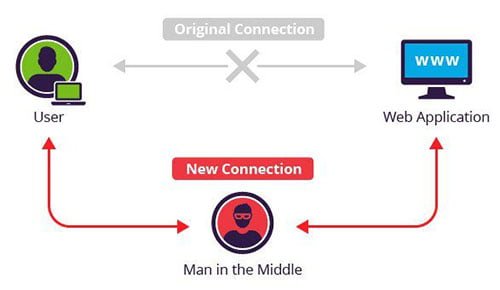
How a MitM (Man in the Middle) is performed with Ettercap
To simulate such attacks we will need two machines victim (A server and a team of that enterprise network), or a router and the machine that will be the victimIncluding also our team. To practice, we can test with three virtual machines, for example.
First, open the Ettercap in its graphical version in the team responsible for carrying out the attack. Normally, usually it runs on Linux. So we follow the steps outlined below:
- Click on the Applications menu.
- Select the Kali Linux / Sniffing / Poisoning Network / Ettercap-graphical program.
- The initial screen of program opens.
- To start working, in the top menu select the Sniff / Unfied sniffing option.
Now we must select the network card or virtual network interface corresponding. The network selected should be one that has been configured with an IP that is within the range of the victim network. Hence, this data should know or find out start. This can be done with many applications for mobile or computers that are on the Internet.
After this step, we are going to new menus appear at the top of the program.
- We mark Hosts / Scan for Hosts to show you the equipment is in that network range. teams with IPS and address appear.
- To choose our goal, we select the correct IP we give the button Add to TARGET1; We can do the same with other Ips.
- Victims to believe that our team is another network, click on the MITM / ARP Poisoning menu.
- We will get another screen where you must select the option Sniff Remote Connections.
- Then, click on the OK button.
- Click on the button on the top menu Start / Start Sniffing.

To verify that we have followed the steps wellOnly we must go to one of the teams that we are spying and open the Run command.
From there we execute an arp and we all computers on the network will appear, including the new IP that has been assigned to spy equipment within our range.
Then we go to a computer screen command and run the command sslstrip. With this we will make SSL secure sites (https) Become simple (http) And thus our Ettercap can get passwords.
For prove that we have done well, Let one of the teams spied upon and try to get into some safe web (Eg Instagram or Facebook). If you look at the log Ettercap we can see that the data entered in the username and password displayed. But by using filters you can access other data such as, for example, If the spying computer accesses a mail server, see data on their inboxes ...

Well, and with this we finish this mini guide how to perform a MITM (Man in the Middle) with Ettercap, You can feel a whole hacker. Did you found it useful? If so feel free to share it and leave a comment. On the other side you can ask any questions or concerns you may have by simply clicking on the link below: contact us. Regards and until next time!