As experts in,,es,industrial network engineering,,es,, we tell you that the company Belden Inc., is the firm responsible for the commercialization, at the beginning of the year, of a robust and compact switch that we love, the,,es,switch industrial Belden MSP40,,en,Características del switch industrial Belden MSP40,,en,This, also known as,,es,switch MSP40 Full Gigabit Ethernet de nivel 3,,en,, is focused on its use in large-scale industrial networks.,,es,Your data transmission speed,,es,It has high-speed ports, something that is above other switches on the market that are also modular and compact. These ports are also interchangeable, a feature that allows you to reach a data rate of up to 2.5 Gb.,,es security in industrial telecommunications networks,,es,we know that living in a society in which the number of intercommunicated mobile devices increases each day until it becomes an indispensable element, it is impossible to deny that the continuous flow of information created by these connections is not important for industrial organizations.,,es,And if this is important, how will the,,es,With a control system, the status of the input variables is evaluated. This information is combined with the man-machine interface requests, a logic is executed (control sequence) and the outputs are updated.,,es,In this context, an interference that attacks the,,es,web security,,es sabemos que viviendo en una sociedad en la que el número de dispositivos móviles intercomunicados aumenta cada día hasta volverse un elemento indispensable es imposible negar que el flujo continuo de información que se crea a raíz de estas conexiones no sea importante para las organizaciones industriales.
Y si este es importante, ¿cómo lo será la security in industrial telecommunications networks,,es,we know that living in a society in which the number of intercommunicated mobile devices increases each day until it becomes an indispensable element, it is impossible to deny that the continuous flow of information created by these connections is not important for industrial organizations.,,es,And if this is important, how will the,,es,With a control system, the status of the input variables is evaluated. This information is combined with the man-machine interface requests, a logic is executed (control sequence) and the outputs are updated.,,es,In this context, an interference that attacks the,,es,web security,,es?
Con un sistema de control se va evaluando el estado de las variables de entrada. Esta información se combina con las peticiones de interfaz hombre-máquina, se ejecuta una lógica (secuencia de control) y con ello se actualizan las salidas.
En este contexto, una interferencia que ataque la seguridad de la web It affects not only the availability as well as the quality of the products that are manufactured but it is possible that facilities, people or even the environment are put at risk.,,es,Corporate information systems and industrial control systems,,es,The performance requirements reliability and risk management in the,,es,they vary depending on the system of which they are part.,,es,In corporate information systems, high performance is always sought, work with data in large volume and with tasks already programmed. The industrial control system works in real time, in a continuous process and with a much smaller data volume.,,es

Sistemas de información corporativos y sistemas de control industrial
Los requisitos de rendimiento fiabilidad y gestión de riesgos en la security in industrial telecommunications networks,,es,we know that living in a society in which the number of intercommunicated mobile devices increases each day until it becomes an indispensable element, it is impossible to deny that the continuous flow of information created by these connections is not important for industrial organizations.,,es,And if this is important, how will the,,es,With a control system, the status of the input variables is evaluated. This information is combined with the man-machine interface requests, a logic is executed (control sequence) and the outputs are updated.,,es,In this context, an interference that attacks the,,es,web security,,es varían en función del sistema del que formen parte.
En los sistemas de información corporativos se busca siempre el alto rendimiento, el trabajo con datos en gran volumen y con tareas ya programadas. El sistema de control industrial trabaja en tiempo real, en un proceso continuo y con un volumen de datos bastante menor.
On the other hand, these systems establish two different priorities. In the case of corporate information systems, the protection of information is prioritized, stopping even all operations if the system is not available.,,es,This interruption can be acceptable, although the recovery of order takes hours (which is not always the case, usually in a matter of minutes everything is solved). The,,es,they have priority 1 the safety of people.,,es,That the system is not available means from the appearance of defects in products, machinery or facilities to a serious danger to people and the environment and the,,es,security in industrial telecommunications networks.,,es,The danger and safety of these systems,,es
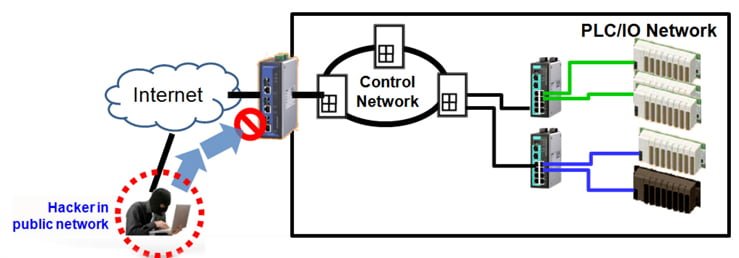
Esta interrupción puede ser asumible, aunque la recuperación del orden lleve horas (que no siempre es así, habitualmente en cuestión de minutos está todo solucionado). Los sistemas de control industrial tienen como prioridad 1 la seguridad de las personas.
Que el sistema no esté disponible significa desde la aparición de defectos en productos, maquinaria o instalaciones hasta un peligro grave para las personas y el entorno y la seguridad en redes de telecomunicaciones industriales.
El peligro y la seguridad de estos sistemas
Determine the possible dangers and impacts requires a categorization of the activities carried out in each place. They are also taken into account in the,,es,the sectors that encompass each activity.,,es,What is the dangerousness of the materials (those that are created and those that are used in the manufacturing process?) What actions make up the productive system? Are the products for human consumption? Are we facing a critical infrastructure? factors to consider.,,es security in industrial telecommunications networks,,es,we know that living in a society in which the number of intercommunicated mobile devices increases each day until it becomes an indispensable element, it is impossible to deny that the continuous flow of information created by these connections is not important for industrial organizations.,,es,And if this is important, how will the,,es,With a control system, the status of the input variables is evaluated. This information is combined with the man-machine interface requests, a logic is executed (control sequence) and the outputs are updated.,,es,In this context, an interference that attacks the,,es,web security,,es los sectores que engloban cada actividad.
¿Cuál es la peligrosidad de las materias (las que se crean y las que se usan en el proceso de fabricación? ¿Qué actuaciones componen el sistema productivo? ¿Los productos son para consumo humano? ¿Estamos ante una infraestructura crítica? Son muchos los factores a tener en cuenta.
Although, by shedding some light, we can say that normally those points likely to create greater risks at the physical level are the least interesting for cybercriminals. Even so, that is no reason to skimp on,,es,There is always going to be a need for a deep security approach that looks at internal and external threats. Next, adequate protection of the type of system is necessary.,,es,It must create, define and maintain a policy of,,es,with which employees are aware, then, in many cases, the human factor is the biggest error in security. Only the,,es,security audits of professional industrial networks,,es,can prevent these increasingly common risks.,,es,2017-06-08T11:01:42 00:00,,en cybersecurity.

Siempre se va a requerir de un enfoque de seguridad profundo que estudie las amenazas internas y externas. Acto seguido es necesaria una protección adecuada al tipo de sistema.
Se debe crear, definir y mantener una política de security in industrial telecommunications networks,,es,we know that living in a society in which the number of intercommunicated mobile devices increases each day until it becomes an indispensable element, it is impossible to deny that the continuous flow of information created by these connections is not important for industrial organizations.,,es,And if this is important, how will the,,es,With a control system, the status of the input variables is evaluated. This information is combined with the man-machine interface requests, a logic is executed (control sequence) and the outputs are updated.,,es,In this context, an interference that attacks the,,es,web security,,es con la que los empleados estén concienciados, pues, en muchas ocasiones, es el factor humano el mayor error en la seguridad. Solo las auditorías de seguridad de redes industriales profesionales pueden prevenir estos riesgos cada vez más usuales.









