For mejorar la seguridad de las comunicaciones industriales it is essential to work on industrial protocols.
As a great difference between OT and IT networks, we have the industrial protocol found in operating networks and that communicates field devices with each other as well as with real-time systems.
These are heterogeneous and insecure, making communications in OT environments difficult to authenticate, authorize, encrypt and audit.
As experts in industrial networks, we know that to solve this, it is necessary to know the ways in which you can improve the security of all industrial communication, starting with said protocols that are equally vulnerable but equally necessary.

Improve the security of your industrial communications
There are three ways to improve the security of industrial communications. Although, this time we will focus on the first one, in a very short time, we will bring you a second part with the remaining two.
Use of specifications associated with secure industry protocols
The best known and most used specifications, in the industrial field, capable of providing the necessary security to the protocols are:
OPC UA
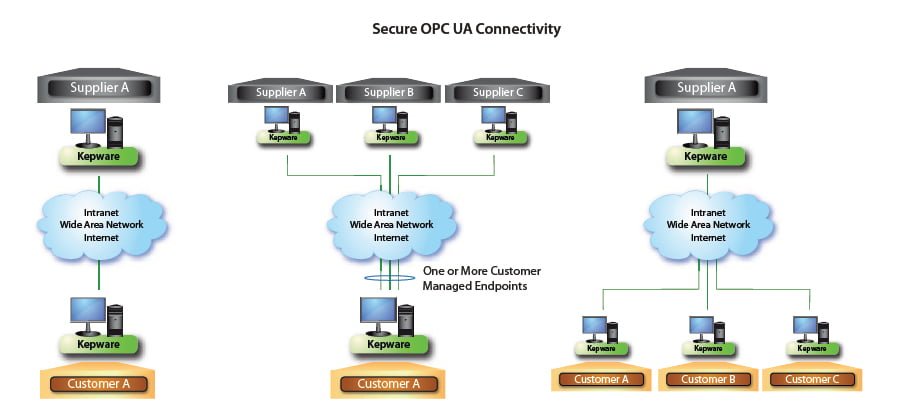
Since 2008 the OPC Foundation It proposes a new specification, the OPC UA or Open Connectivity Unified Architecture, whose objective is to improve and evolve the total of the traditional OPC specifications. For this, the following is proposed:
- Integrate the OPC specifications (DA, HDA and A&E) in one.
- Create an independence of the operating system in question, thus dissociating itself from Microsoft.
- Use a service-based style to integrate data and applications, such as Web Services.
- Use HTTP protocols that facilitate accessibility to OPC applications, as these are a basic pillar of web services.
- Include a native security layer for the specification, capable of providing communications with confidentiality, authentication, integrity, availability and auditability.
Secure DNP3
A year earlier, in 2007, the specification Secure DNP3 (I have made two articles of courses where it is included but I cannot find them on the web to link them) It was published as a solution to be used in both DNP3 Serial and DNP3 encapsulated over TCP.
It is based on IEC 62351-5, managing the security of TC 57 protocols: IEC 60870-6 series, IEC 61850 series, IEC 61968 series e IEC 61970.
With this protocol you can:
- Authorize and authenticate all communication between master and slave using a pre-shared key.
- Periodically authenticate and authorize master-slave communications with HMAC.
- Authorize and authenticate critical request and responses between master and slave (Writes, selects, operates and direct operates, start, stop, initialize, enable and disable, cold restart, warm restart, authenticate file, activate…).
We must end by mentioning that the information is encrypted by TLS, not Secure DNP3, defining this specification in IEC 62351-3.
We will soon continue this interesting post about cómo mejorar la seguridad de las comunicaciones industriales with two other interesting actions: the incorporation of specific technologies and the fortification of the servers. Do not miss it!









